|
[Update 1: The authors of this software were notified, thanked me for my short analysis, and told me they will use my remarks to improve the steganography method. I'm not saying that for a cheap ego trip, it's because I'm so bored to see editors suing people who point out weaknesses in their products. Intelligent security software makers, as people from Neobyte just proved it, use constructive criticism to improve their programs. Update 2: They sent me a new email to tell me that they have now fixed one of the weaknesses I pointed out here (filling unused LSBs with a fixed pattern in BMP images), in their new version 4. Great! So keep in mind the following results are about an old version]. |
1. Background
Invisible Secrets 2002 is a shareware (sold US$35) by Neobyte Solutions (ex-"East-Tech" for those who remember their very good Eraser program). The demo version is time limited, 30 days, enough for me to do a few tests. It has a very good interface and plenty of options if you want to play with, clearly a professional work.
Invisible Secrets 2002 bundles a lot of things together, and I need to make it clear that I didn't test everything this software has to offer, like for example, the password management. My main interest here is the steganography strength. And, if a lot of things are very good in this software in terms of security and ergonomy, curiously the steganography methods used are not as good, and the result is that it's really evident to see that there is hidden data in files.
2. So what's good?
Quickly, because it's not my main point, the good ideas related to security:
1. Use of strong cryptography symetric algorithms (including Blowfish, Twofish, RC4, AES, and others) by default. You can use it as a stand-alone encryption software. Other algorithms may be added later by using libraries.
2. A good file wiper is included.
3. Five possible carrier files (JPEG, PNG, BMP, HTML and WAV), but what is especially interesting is the possibility to add new ones later (or to update the actual algorithms, which is needed in my opinion).
4. Compression of data before hiding. A simple and important step (and often forgotten) to reduce the size and the redundancy of the hidden data (thanks to Bart Bailey for pointing out my sloppy use of the term "entropy" here).
5. Possibility to hide "fake files" (random files) along with your genuine files, to increase the noise.
2. And what's bad?
1. PNG and JPG "steganography" is really bad: the hidden data is placed in the comment field of these file image types (which is located at the beginning of the file for JPG, at the end for PNG). Just to compare, BMP and WAV use a 1-bit LSB method, and HTML uses spaces / tab (0/1) added at the end of the lines.
2. The hidden data, even if the content is heavily encrypted, still has a fixed and linear structure (even if it starts from the last line of the image). So it's very easy to see that you're hiding something, and that you used this particular program.
3. An idea so bad I cannot even understand how these fine programmers got it: in the BMP images, the LSBs not used by the hidden data are all set to 1 or 0. It's not even needed to modify these bits. That's like saying: "Hey, look here!".
If you don't get why it is a bad idea, here is a visual response:

|
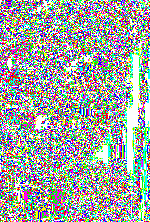
|

|

|
| This is the original image, a JPG version of the original BMP. In case you don't know, this is french actress Audrey Tautou in "Amélie". | These are the enhanced LSBs of the original image, using this small tool. | These are the enhanced LSBs of the same image with one file hidden (the top random bytes). The non-used LSBs are filled with 0's (so what's not used is black). | These are the enhanced LSBs of the same image with a bigger file hidden. This time the non-used LSBs are filled with 1's (so what's not used is white). |
3. How to see there is something hidden?
I'm not going to detail everything like before. Just the general idea, for BMPs. The structure of the raw hidden data appears to be the same for all carriers (to be frank, I didn't check for WAV's).
1. Jump to the last line.
2. Extract all the least significant bits in order.
3. When you get at the end of the line, jump to the precedent line and start again.
4. Now you have extracted the raw data.
5. Check the size of the encrypted header, jump over it to get the next size.
6. Continue to jump over all data blocks (encrypted or not) until you find yourself in a sea of identical bits. If you get there, then there is probably something hidden by Invisible Secrets 2002.
4. My Invisible Secrets 2002 Hidden Data Finder
I rapidly coded a small software called "Invisible Secrets 2002 Hidden Data Finder", with source, to automatize the process. Here is what it's doing:
=> if the file is not a 24-bits BMP, it says so and stops.
=> if the hidden data does not look like Invisible Secrets 2002 hidden data, it says so and stops.
=> if the hidden data looks like Invisible Secrets 2002 data, it says so and extracts it in a raw binary file under the name "hidden_extracted.bin", so you can check it.
Have a nice day!
Guillermito, September 23th 2002